
Let’s Network
 jonas
jonas- HomeLab
- February 2, 2025
One thing I needed to redo was my home network. Obviously, running my cluster directly inside my home network would be way too simple. So, I went for something a bit more interesting. The plan? Separate the home cloud from the rest of the network. Technically, this could be called a demilitarized zone (DMZ)—but my setup is a little more… obfuscated.
Overview
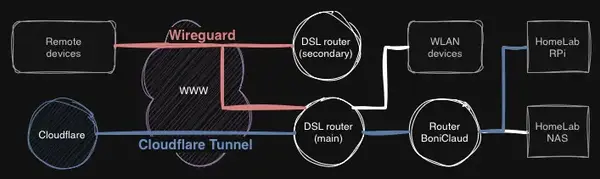
Right now, my setup consists of three routers:
- Two routers are connected to the internet, and they’re linked together via WireGuard VPN.
- Any mobile device outside my home network can also connect via WireGuard.
- Behind the main router is my home network.
- The boniclaud router serves as both a switch and firewall for all BoniClaud devices.
Why go through all this trouble? Security and flexibility. This setup lets me experiment with BoniClaud services without exposing my entire home network. BoniClaud can’t access my home devices, and only services within its network are exposed to the internet. Plus, having a dedicated router makes it easy to test networking setups without risking misconfigurations of the who.e network.
WireGuard VPN
Let’s start with WireGuard. It’s a modern, open-source VPN that’s widely supported and, most importantly, easy to set up.WireGuard gives me two big advantages:
Secure Browsing Anywhere
I don’t always trust the networks I connect to (looking at you, shady hotel WiFi). With WireGuard, I always have a secure connection to my home router. As long as I trust my home router’s connection to my ISP, I’m good.
Public WiFi networks can have sniffers that track which sites you visit. I’m the worst case Man-in-the-middle attacks could even try to decrypt your data. And even if my browsing is completely harmless, that doesn’t mean someone else needs to keep tabs on it.
Seamless Remote Access to My Home Lab
The really cool part? WireGuard makes my remote device act like it’s inside my home network. That means I can access any BoniClaud service without exposing it to the internet. For example, my photo cloud stays private but remains accessible from anywhere. Instead of exposing services publicly, I just keep them local and use WireGuard to access them remotely.
Netflix Bridge
Now, this is where things get fun. You’ve probably know that Netflix only allows account sharing within a single household. But what does Netflix consider a household? Simple: any devices connected to the same internet-facing router. If you link two routers via WireGuard, you can configure certain devices to route their traffic through the other router first. The result? The device appears to be in the same “household.”
You don’t need to modify the device itself—no special apps, VPNs, or browser settings. The setup is handled entirely at the network level, so even a normal smart TV can connect seamlessly.
Is this a hack? Honestly, I think Netflix just can’t detect it. From a professional standpoint, VPNs are commonly used to link multiple company sites into one network. Each office has its own internet connection, but they’re still part of the same corporate network. So, if I interconnect my private network with another one, technically, that’s still one household—just split across multiple locations.
For now, the setup works. If Netflix ever gets better at detecting VPNs, I’ll just have to get more creative.
Ad-Blocking
Now for something completely different. With my multi-site household connected and secure remote access enabled, what else can I tweak? A lot of ads and tracking scripts aren’t directly embedded into websites—they’re loaded dynamically from ad servers. If those servers are blocked, no ads can be displayed.
Setting Up DNS-Level Ad Blocking
- The BoniClaud router runs a DNS server that filters out known ad and tracking domains.
- If a device requests a blocked domain, the DNS simply responds with “not found.”
- This removes ads and speeds up website loading (some ad-heavy sites load almost twice as fast).
The Catch? Sites that have the ads directly embedded into their content cannot be blocked. For example YouTube ads can’t be blocked since they’re embedded inside the video stream. Some mobile games break when ad servers are blocked. Many apps just crash instead of handling the failure properly. Other websites refuse operation or if you are lucky just ask you to turn off your ad-blocker. As a workaround my guest WiFi uses a different DNS setup that allows ads, so mobile games can be -payed and websites used, as long as you connected to that WiFi.
Firewalling BoniClaud
Finally, let’s talk about firewalling BoniClaud—because everything up to now wasn’t really related to BoniClaud.
BoniClaud shouldn’t have access to my home network. It should only be able to access the internet. This isn’t just for security reasons (though that’s part of it). It also helps prevent misconfigurations from messing up my entire network. Let’s be real—an accidental setting tweak is far more likely than a targeted attack on my infrastructure.
The internet-facing router blocks all incoming connections by default (good). Only the Cloudflare Tunnel handles external access, so I don’t need to open any ports on the router. A dedicated firewall sits between BoniClaud and my home network. It treats BoniClaud like the internet—it can’t see my home devices. However, my home network can access BoniClaud if needed.
OpenWRT: Taking Control of the Network
To make everything even more configurable, the BoniClaud router runs OpenWRT—an open-source router firmware with a huge community and tons of plugins.
I repurposed an old router, flashed OpenWRT onto it, and now it’s handling all BoniClaud traffic. The downside? The router’s WiFi chip isn’t supported, so it’s wired-only—but BoniClaud doesn’t need WiFi anyway. The bonus? With local DNS resolution for BoniClaud services, I don’t need to route through Cloudflare tunnels when accessing the blog from the home lab. And the Network-wide ad blocking plug-in runs directly on the router (unfortunately large block lists slow down DNS queries—some requests take seconds to resolve).
Conclusion
Networking is fun, but let’s be honest—most of this is completely unnecessary for a home setup.
For 99% of people, this level of complexity has no real advantage. But that’s not the point of my homelab. The point? Solving problems that don’t exist.